The rise of crypto ransomware attacks
Ransomware attacks continue to plague the cryptocurrency world, and one of the most notable players is the BlackCat group.
Ransomware attacks targeting cryptocurrencies have become widespread. Crypto, being anonymous and decentralized, is attractive to cybercriminals. They increasingly favor crypto’s relative anonymity and ease of cross-border transfer.
Ransomware groups, including the BlackCat, exploit these features by demanding payments in crypto, making it harder for authorities to trace and recover stolen funds. There has been a significant spike in the frequency and severity of attacks in 2024.
Chainalysis’ cryptocurrency-cybercrime report pointed to this growing trend:
- $1.9 billion in ransomware payments recorded in 2024 by mid-year, an 80% increase from the previous year.
- The average ransom demand rose 30% in 2024, reaching nearly $6 million per attack.
It wasn’t just corporations like MGM Resorts or UnitedHealth victimized by ransom demands for millions of dollars in Bitcoin and other cryptocurrencies. Even individual investors are being targeted. Cybercriminals are using increasingly sophisticated tactics, like double extortion, where hackers encrypt data and threaten to release sensitive information unless an additional payment is made.
How can the crypto industry fight back against these sophisticated attacks? Dive deep into BlackCat’s crypto-ransomware attacks, see how the group operates and discover what can be done to protect against these increasing blockchain threats.
BlackCat ransomware attack explained
BlackCat ransomware, also known as Noberus or ALPHV ransomware, is a type of malware created by a group of Russian-speaking cybercriminals.
BlackCat is a highly sophisticated ransomware-as-a-service (RaaS) group that has repeatedly made significant headlines for its devastating attacks in the cryptocurrency world. The group first appeared in November 2021 and has since targeted hundreds of organizations worldwide, including Reddit in 2023 and Change Healthcare in 2024.
BlackCat operates via a defined modus operandi — infiltrating systems, encrypting data, and demanding hefty ransoms paid in crypto to restore access. What sets BlackCat apart from other ransomware is its advanced coding structure and customizable attack methods, which are often tailored to the vulnerabilities of each target, making it highly effective.

When it started, BlackCat was designed to support a wide range of operating systems, from Windows to Linux, using the rare Rust programming language, which allows for great flexibility and speed in encryption.
By 2024, BlackCat escalated its efforts, exploiting weaknesses in both corporate infrastructures and crypto platforms. The attacks often follow a double extortion model, where not only is data encrypted, but sensitive information is stolen and followed by threats to leak it unless an additional payment is made. This tactic gives the group immense leverage over its victims.
What makes BlackCat even scarier is the way the model operates. They have a decentralized affiliate model, which means they recruit hackers globally who can synchronize and carry out attacks on their behalf, each with customizable payloads. In short, BlackCat knows how to find vulnerabilities and hit where it hurts.
Did you know? The US Department of State is offering a reward of up to $10 million for information leading to the identification or location of individuals in key leadership positions within the group behind the BlackCat ransomware attacks.
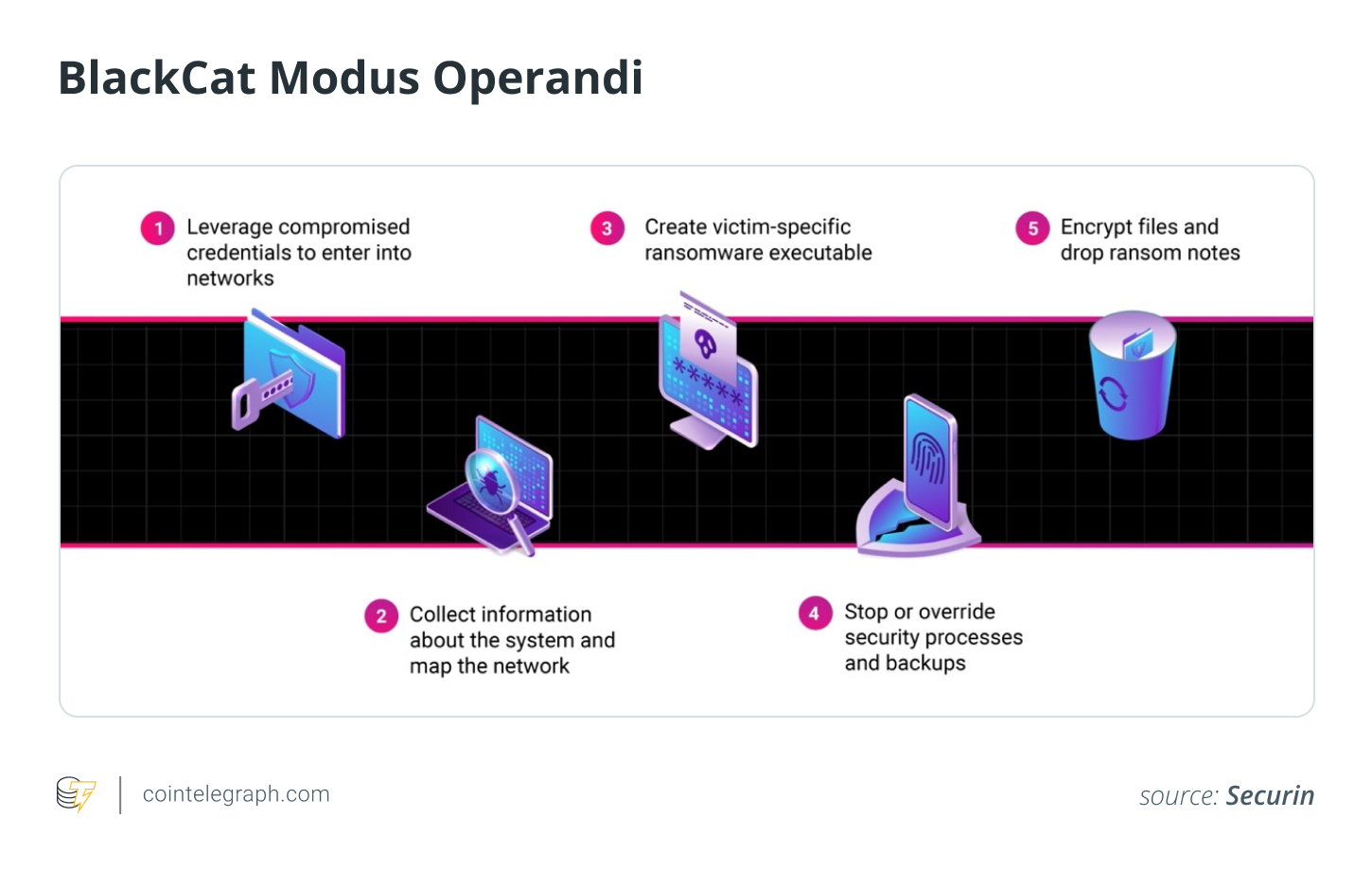
How BlackCat ransomware works
BlackCat ransomware is known for its meticulous and calculated approach to cybercrime, making it a formidable threat in the digital landscape.
Here’s a breakdown of how BlackCat ransomware operates:
- Initial access: BlackCat typically infiltrates systems through phishing emails, stolen credentials or exploiting unpatched vulnerabilities.
- Establishing persistence: Attackers install backdoors to maintain access and harvest credentials for lateral movement within the network.
- Data encryption: Using the Rust programming language, BlackCat encrypts important files, rendering them unusable without the decryption key.
- Double extortion: Attackers steal data before encrypting it, threatening to leak it if the ransom is not paid.
- Ransom demands: Payments in cryptocurrencies like Bitcoin (BTC) or Monero (XMR), equating to millions of dollars, are demanded, ensuring the attacker’s anonymity.
- Customizable attacks: Affiliates can tailor the ransomware to specific victims, targeting Windows or Linux platforms with advanced techniques to avoid detection.
Victims are required to pay ransoms in cryptocurrency, allowing for anonymity and making it nearly impossible for authorities to track or recover the funds. BlackCat’s impact on the crypto space is a reminder of the importance of securing digital assets and infrastructure against these ever-evolving cyber threats.
Did you know? BlackCat’s use of Rust programming language gives it the flexibility to target both Windows and Linux systems, making it more adaptable than other ransomware.
BlackCat affiliates model
Affiliates are independent hackers who partner with the BlackCat group, leveraging its sophisticated RaaS model and tools.
BlackCat’s operations thrive on an affiliate model, where multiple actors contribute to its widespread reach. Here’s how that works:
- Affiliate program: Cybercriminals sign up for BlackCat’s program to access and distribute ransomware payloads.
- Profit-sharing model: Affiliates earn a significant portion of any ransom they collect, while a share is sent to the BlackCat developers.
- Double extortion tactics: Affiliates often use a two-pronged approach by encrypting data and threatening to leak it unless the ransom is paid.
- Customizable payloads: BlackCat provides affiliates with the ability to customize ransomware for specific targets, making attacks harder to defend against.
- Cryptocurrency payments: Affiliates demand ransoms in crypto, which provides anonymity and makes tracing payments exceedingly difficult.
This affiliate model has enabled BlackCat to scale rapidly and attack a variety of high-value targets across different sectors.
BlackCat ransomware institutional attacks
The BlackCat group has managed to target high-profile organizations, causing significant operational and financial impacts.
Below are some notable case studies that illustrate the reach and severity of BlackCat’s institutional attacks:
- Oil tanking group and Mabanaft attack: BlackCat struck OilTanking Group and Mabanaft in early 2022. The attack shut down their fuel storage and distribution systems, significantly disrupting supply chains in Germany. The hackers demanded a substantial ransom to release encrypted systems, though the exact amount was not widely disclosed (with 5-7 days allotted to purchase Bitcoin or Monero cryptocurrency for making ransom payments). No arrests were reported in connection with this attack.
- MGM Resorts and Caesars Entertainment: In September 2023, BlackCat was involved in a high-profile ransomware attack on MGM Resorts International and Caesars Entertainment. The stakes were high — Caesars initially faced a demand for $30 million in Bitcoin but managed to negotiate down to $15 million. MGM Resorts, however, refused to pay the ransom, leading to weeks-long operational shutdowns and a financial loss of $100 million for the quarter. This attack was executed by the BlackCat affiliate Scattered Spider, a group of American and British hackers.
- Change Healthcare: In early 2024, BlackCat attacked Change Healthcare, a subsidiary of UnitedHealth Group, resulting in the theft of sensitive patient data and operational disruptions. To recover their systems, Change Healthcare reportedly paid a $22 million ransom in Bitcoin. This event highlighted the growing risk of ransomware attacks in the health-care sector and the precarious position companies are in when dealing with these cybercriminals.
Protect against BlackCat ransomware
Understanding root causes and how ransomware operates is the first step toward protecting against them.

To protect against BlackCat ransomware, it is critical to avoid mistakes and take protective measures, including:
- Regularly back up your data: Frequent, encrypted backups stored offline can be a lifeline if your files are encrypted.
- Establish strong cybersecurity protocols: Ensure the organization’s cybersecurity team conducts regular vulnerability assessments and enforces security protocols like multi-factor authentication and network monitoring.
- Employee training: The team should also provide training to employees to ensure everyone understands and follows security best practices across official work channels and platforms.
- Install antivirus software: A robust antivirus system can help detect and stop the malware before it encrypts your files.
- Cautious of phishing attempts: Be active in spotting and avoiding phishing emails that might carry ransomware payloads.
- Employ password management systems: Enforcing regular password updates can prevent cybercriminals from gaining access to accounts.
- Segment your network: Isolating parts of your network can limit the spread of ransomware.
Despite facing crackdowns from international law enforcement, BlackCat remains a significant threat in 2024. Therefore, cryptocurrency users must remain vigilant, strengthen their cybersecurity measures, and stay updated on evolving ransomware threats.