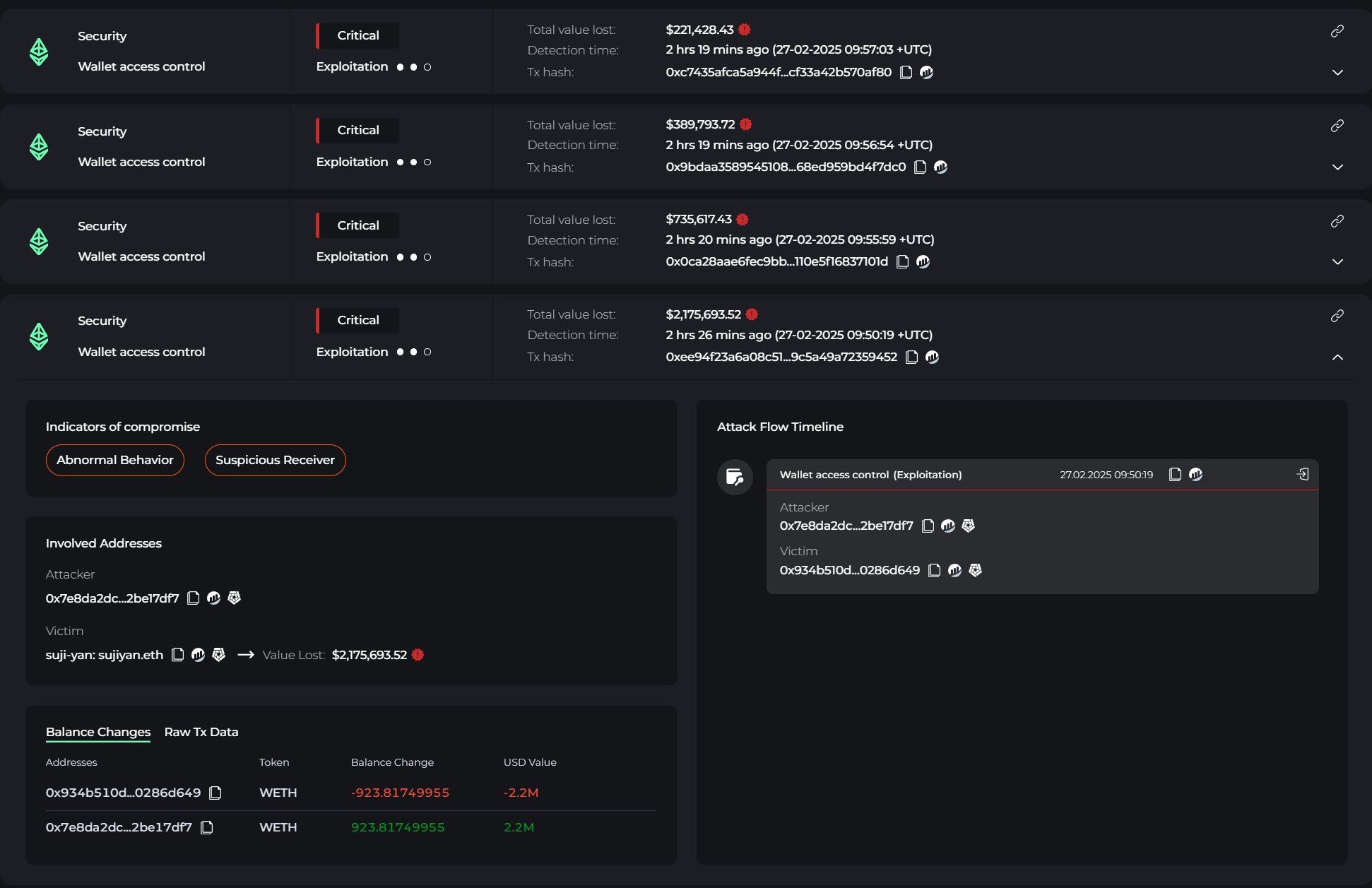
Onchain cybersecurity platform Cyvers detected suspicious outflows on Feb. 27 from an address linked to Mask Network founder Suji Yan.
According to Cyvers, other flagged addresses had received about $4 million in cryptocurrencies, primarily in Ether (ETH)-linked tokens.
The digital assets suspected to have been stolen included 113 ETH, valued at over $265,000 at the time of writing, 923 WETH, 301 ezETH, 156 weETH, 90 pufET, 48,400 MASK, 50,000 USDt (USDT) and 15 swETH.
Tracing the compromised transaction flow. Source: Cyvers Alerts
Following the initial compromise, the funds were then swapped to ETH and funneled through six different wallet addresses, with one of the offending wallets ending in “df7.” Meir Dolev, co-founder of Cyvers, told Cointelegraph:
“This incident underscores the increasing sophistication of threat actors in the Web3 space and highlights the urgent need for real-time transaction monitoring, preemptive prevention and rapid incident response.”
This incident is the latest in a string of recent high-profile hacks and exploits, including the $1.4 billion Bybit hack on Feb. 21 and the Pump.fun social media hack on Feb. 26.
Related: From Sony to Bybit: How Lazarus Group became crypto’s supervillain
Crypto industry rocked by sophisticated hacking techniques
Forensic investigations into the recent Bybit hack show the exploit occurred due to compromised credentials of a SafeWallet developer and targeted the Bybit team.
According to a statement released by the Safe team, the exploit did not affect any of the code for its front-end services or its smart contracts.
Instead, the hackers used the compromised system to attack the user interface — sending seemingly legitimate transactions to Bybit and then diverting the funds from the malicious transactions to a different hardware wallet.
However, Martin Köppelmann, the co-founder of the Gnosis blockchain network, which developed and spun off Safe, said that he could only speculate how the hackers used the exploit to trick multiple signers from the Bybit team.
The crypto executive added that the Lazarus Group, strongly believed to be behind the attack, likely avoided attacking other accounts using Safe products to avoid detection and giving away their tactics.
Magazine: 2 auditors miss $27M Penpie flaw, Pythia’s ‘claim rewards’ bug: Crypto-Sec