Hackers are creating hundreds of fake GitHub projects aiming to dupe users into downloading crypto and credential-stealing malware, says cybersecurity firm Kaspersky.
Kaspersky analyst Georgy Kucherin said in a Feb. 24 report that the malware campaign, which the company dubbed “GitVenom,” has seen hackers creating hundreds of repositories on GitHub hosting fake projects that contain remote access trojans (RATs), info-stealers and clipboard hijackers.
Some of the faked projects include a Telegram bot that manages Bitcoin wallets and a tool to automate Instagram account interactions.
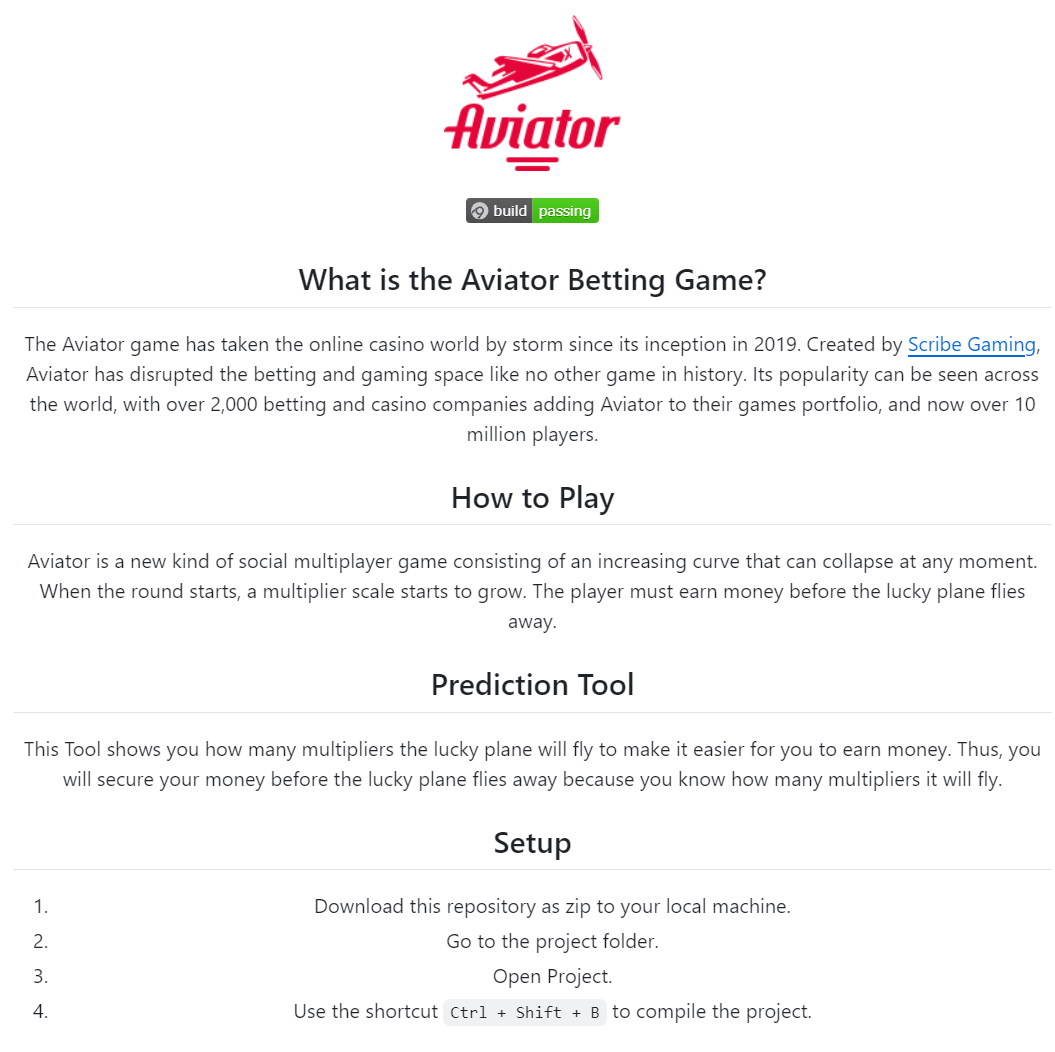
Kucherin added the malware makers “went to great lengths” to make the projects look legitimate by including “well-designed” information and instruction files that were “possibly generated using AI tools.”
Those behind the malicious projects also artificially inflated the number of “commits,” or changes to the project, alongside adding multiple references to specific changes to give the appearance that the project was being actively improved.
“To do that, they placed a timestamp file in these repositories, which was updated every few minutes.”
An example of what Kaspersky said is a “well-designed” instruction file included in what presents as a betting game. Source: Kaspersky
“Clearly, in designing these fake projects, the actors went to great lengths to make the repositories appear legitimate to potential targets,” Kucherin said in the report.
The projects didn’t implement the features discussed in the instruction and explainer files, with Kaspersky finding they mostly “performed meaningless actions.”
During its investigation, Kaspersky found several fake projects dating back at least two years and speculated the “infection vector is likely quite efficient” because the hackers have been luring victims for quite some time.
Regardless of how the fake project presents itself, Kucherin said they all have “malicious payloads” that download components such as an info stealer that takes saved credentials, cryptocurrency wallet data, and browsing history and uploads it to the hackers through Telegram.
Another malicious component uses a clipboard hijacker that seeks crypto wallet addresses and replaces them with attacker-controlled ones.
Kucherin said these malicious apps snared at least one user in November when a hacker-controlled wallet received 5 Bitcoin (BTC), currently worth around $442,000.
The malware collects information such as saved credentials, crypto wallet data and browsing history, then uploads it to the hackers through Telegram. Source: Kaspersky
The GitVenom campaign has been observed worldwide but has an elevated focus on infecting users from Russia, Brazil and Turkey, according to Kaspersky.
Related: Ransomware losses down 35% year-over-year: Chainalysis
Kucherin says because code-sharing platforms such as GitHub are used by millions of developers worldwide, threat actors will continue using fake software as an infection lure.
He advised that it was essential to check what actions any third-party code performs before downloading.
Kucherin added the company expected attackers to continue publishing malicious projects, but “possibly with small changes” in their tactics, techniques, and procedures.
Magazine: ETH whale’s wild $6.8M ‘mind control’ claims, Bitcoin power thefts: Asia Express